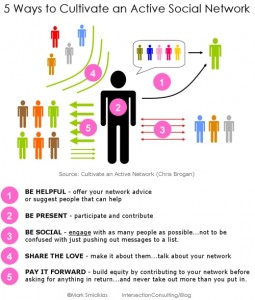
The other day, I received a question regarding how all this Twitter stuff works. I spent a little time explaining the concepts and then decided that I should write a blog about it. I’m sure everyone would like to hear about Twitter and how it’s being used for Social Networking and Social Marketing.
Continue reading
-
Archives
- December 2016
- April 2012
- May 2011
- April 2011
- February 2011
- January 2011
- December 2010
- November 2010
- October 2010
- September 2010
- August 2010
- July 2010
- June 2010
- May 2010
- April 2010
- March 2010
- February 2010
- January 2010
- December 2009
- November 2009
- October 2009
- September 2009
- August 2009
- July 2009
- June 2009
- May 2009
-
Meta